Large language models bolster the security of IoT devices, but their recommendations must be validated by human expertise prior to implementation.
he Internet of Things (IoT) is a network of physical objects that can connect and exchange data with other devices and systems over the internet. These can range from ordinary household objects to sophisticated industrial tools. IoT finds applications in various industries, including smart homes, wearable devices, smart cities, and Industrial IoT.
IoT is a rapidly growing field with the potential to revolutionise many industries and aspects of our lives. IoT devices can enhance our lives by increasing the efficiency and security of our homes and businesses, making our cities more livable, and facilitating proactive healthcare systems.
Why IoT security?
IoT devices play a critical role in essential infrastructure, such as energy grids, transportation systems, manufacturing plants and healthcare. Unauthorised access to these systems can result in severe repercussions, including power failures, transportation disruptions, and potential loss of life. Hence, protecting data, privacy, and the functionality of IoT devices is crucial.
In addition, IoT devices are often integrated into enterprise networks, creating a pathway for attackers to infiltrate and compromise corporate networks, leading to data breaches, and intellectual property theft.
Hence, as IoT devices proliferate, addressing IoT security challenges becomes increasingly important.
How is IoT security different from traditional security?
IoT security differs from traditional security in several ways due to the unique characteristics and challenges presented by IoT devices and ecosystems. Here are some of the primary differences between IoT security and traditional security.
- Attack surface: IoT devices are often connected to the internet, creating a much larger attack surface compared to traditional devices.
- Resource constraints: IoT devices frequently have limited computing, memory, network, and energy resources, which restrict the ability to implement complex security measures.
- Heterogeneity: IoT devices come from various manufacturers, featuring different operating systems and security features, making it challenging to uniformly implement traditional security measures.
- Physical environments: IoT devices are often deployed in diverse and difficult-to-access remote locations, making them susceptible to physical tampering and environmental factors that traditional IT infrastructure may not encounter.
- Scale and quantity: IoT networks can consist of thousands or even millions of devices, far exceeding the scale of traditional IT devices and networks. Managing and securing this large number of endpoints poses a significant challenge.
Additionally, there are other challenges like life cycle management, supply chain vulnerabilities, and the lack of proper user interfaces.
Traditional security solutions are designed to protect IT systems such as enterprise networks, servers, and workstations and are not effective at safeguarding IoT devices due to these unique challenges.
How to ensure IoT security
Securing IoT requires a tailored approach, including measures such as device authentication, encryption, secure device management and regular updates.
- Device security: IoT devices need security at the hardware and software levels. We need to implement lightweight embedded agents that can keep the device’s operating system and software up-to-date. In addition, they should offer runtime protection to monitor state, and respond when there are anomalies detected to identify and combat zero-day attacks.
- Network security: We need to implement a zero-trust strategy and segment the network to isolate IoT devices from other devices, minimising the attack surface.
- Firmware security: In-depth examination of an IoT device’s firmware should be conducted to detect potential vulnerabilities within its code.
IoT security solutions should also include auto device discovery and identification, secure firmware updates, and real-time monitoring and anomaly detection, using security information and event management systems to collect and analyse log data from IoT devices.
IoT security with LLMs
LLMs (large language models) are AI models based on artificial neural networks, trained using self-supervised learning and semi-supervised learning. As autoregressive language models, they work by taking an input text and repeatedly predicting the next token or word. They have the potential to significantly impact IoT security in various ways.
- Automated threat detection: LLMs can be used to develop natural language processing models to analyse logs, reports, and security alerts from IoT devices and networks. This can help in automated threat detection and response by identifying patterns and anomalies in textual data.
- Automated patch management: These models can automate security tasks like vulnerability scanning and improved patch management of IoT devices.
- Security awareness and education: LLMs can generate educational content, articles, and documentation about IoT security to raise awareness and understanding of IoT security best practices.
- Comprehensive security policy development: They can assist in creating and refining security policies and guidelines for IoT deployments.
- Secure configuration templates: LLMs can help generate secure templates for IoT devices and provide guidance on how to configure devices for better vulnerability management.
LLMs also have the potential to be used to develop new and more sophisticated IoT attacks that can have an adversarial impact on IoT security.
- Adversarial attacks: LLMs can be manipulated to generate deceptive content, including phishing emails, fake security advisories and malicious code that can lead to social engineering attacks against IoT users.
- Automated exploitation: LLMs can be used to automate malicious tasks, such as scanning for vulnerable IoT devices and exploiting them.
- Privacy concerns: Conversations between users and AI systems can disclose sensitive information about IoT devices and their vulnerabilities.
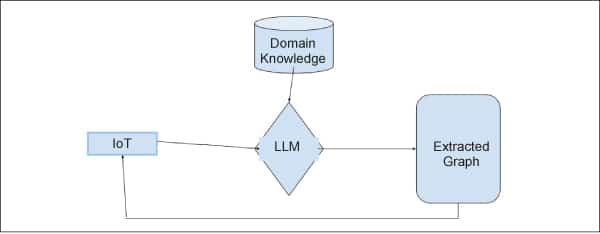
LLMs are proving to be highly effective at solving general-purpose tasks since they are trained on large data sets based on a broad generalist knowledge base. However, their ability to access specialised, private, and up-to-date knowledge is limited. To enhance LLM knowledge in a specific domain, fine-tuning them on domain-specific data sets is crucial.
It is important to use LLMs judiciously in IoT security to maximise their positive impact and mitigate the challenges. Human expertise is essential to validate the recommendations and findings generated by AI models. This includes implementing safeguards to prevent adversarial attacks, curating AI-generated content, and ensuring human oversight in critical security decision-making processes.
IoT security is expected to evolve in response to the growing number of IoT devices and the increasing complexity of IoT ecosystems. Following are some key trends and developments that will guide the future of IoT security.
- Increased adoption of zero trust security with a focus on continuous verification and strict access controls for both devices and users
- Implementation of enhanced authentication methods like multi-factor authentication, biometrics, and hardware-based authentication
- Blockchain technology using tamper-proof ledgers for device identity, transactions, and data integrity to help secure device updates and firmware integrity
- AI and machine learning algorithms to help identify abnormal behaviour and potential threats in real-time
- Edge computing security solutions to protect data and devices at the source
- Comprehensive device life cycle management, including secure onboarding, patching, and end-of-life decommissioning
- Introduction of stricter IoT security regulations and standards by governments and regulatory bodies to safeguard data and privacy
- Secure coding practices and rigorous security testing embedded into the development process
- Post-quantum cryptography to secure IoT data against quantum attacks
Overall, IoT security requires a proactive and holistic approach to address the unique challenges posed by IoT ecosystems. As LLMs continue to develop, they will play an innovative role in protecting IoT devices and networks. Incorporating LLMs into IoT security operations requires careful planning, integration with existing security infrastructure, and ongoing monitoring to ensure that AI-generated insights align with the unique security requirements of IoT ecosystems.
Disclaimer: The views expressed in this article are that of the author and Palo Alto Networks does not subscribe to their substance, veracity or truthfulness.